Secure Onboarding: Best Practices for Protecting Data with Remote Hires

- 1. Implement a Robust Identity Verification Process
- 2. Use Secure Communication Channels
- 3. Leverage Secure Access Control
- 4. Secure Endpoint Management
- 5. Provide Cybersecurity Training for Remote Hires
- 6. Implement Remote Work Policies
- 7. Monitor and Audit Remote Employees' Activity
- 8. Use Digital Signatures and Contracts

 Cut onboarding time
by 60%—here's the
Ultimate Checklist
that helped do it.
Cut onboarding time
by 60%—here's the
Ultimate Checklist
that helped do it.
The option of working from home has made remote employees an essential aspect of many organizations, allowing companies to hire talent worldwide. However, this digital transformation introduces cybersecurity issues, particularly at the onboarding stage. Secure remote onboarding is crucial for protecting company data, fostering trust, and ensuring regulatory compliance.
In this article, we will explore the onboarding best practices for securing the remote onboarding process and safeguarding your company's sensitive data.
1. Implement a Robust Identity Verification Process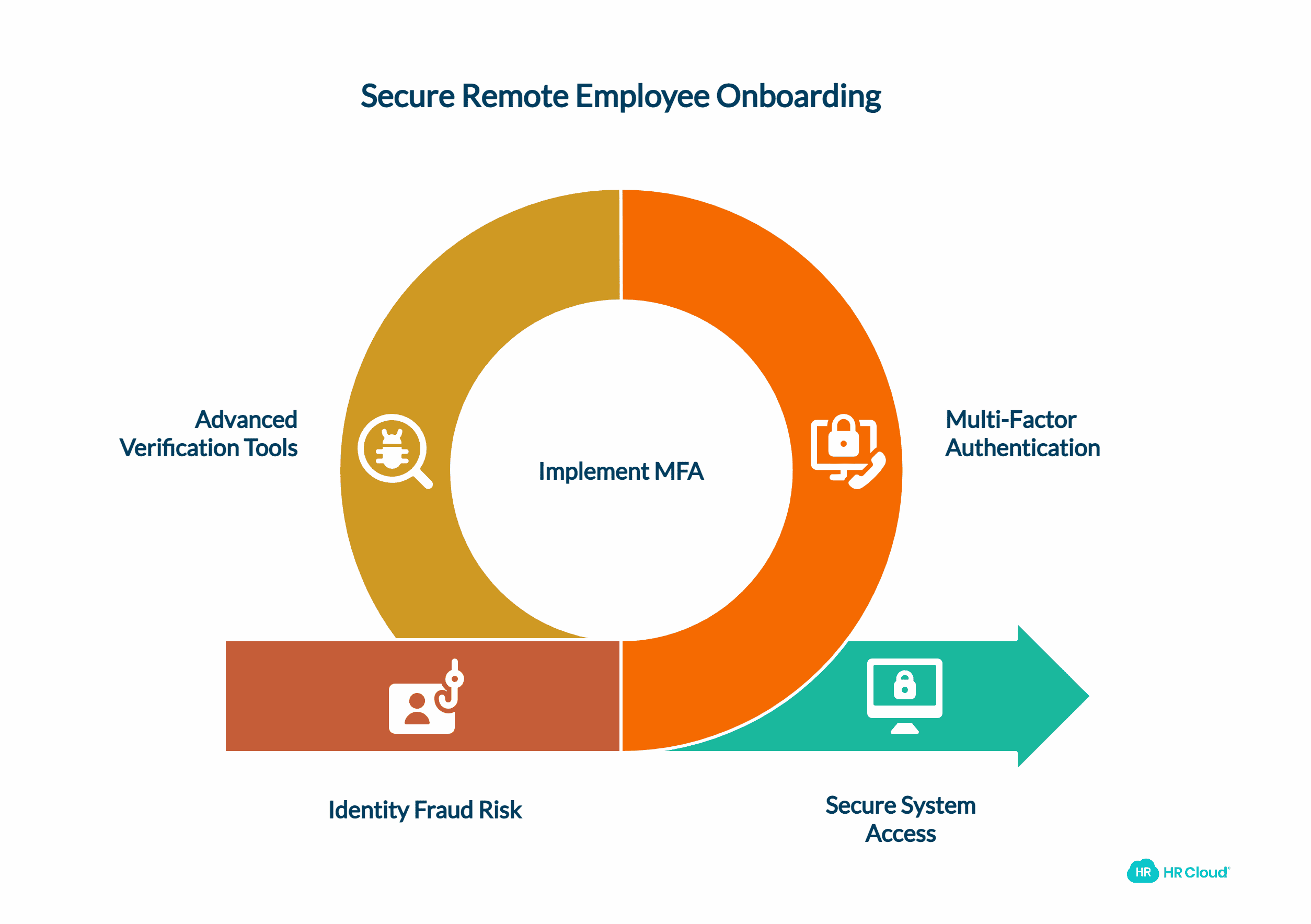
In onboarding new remote employees the first step in data protection involves ensuring the identity of the new joining member of the organization. With the recent developments in digital interactions, fraudsters have an opportunity to masquerade as genuine candidates.
Implementing a robust digital identity verification process reduces the dangers of identity fraud and allows only the right people to enter your company's systems. Employing multi-factor authentication (MFA) at the beginning of the identity verification process is one of the most effective solutions. MFA requires the user to provide at least two factors of identity, such as a password and a fingerprint scan, to access the systems. This added security feature makes it even harder for a hacker to impersonate an employee, even if they obtain the login information.
To further enhance security, consider using advanced identity verification tools and biometric verification methods. These digital tools can help streamline the identity checks process while maintaining high security standards.
2. Use Secure Communication Channels
Communication is crucial during the digital onboarding process, which is why there should be an emphasis on using secure methods to transmit information such as personal details and sensitive data. Avoid sharing protected materials via email or open messaging applications.
Instead, use encrypted communication channels for sharing sensitive information. Various secure platforms are available now, including Zoom, Slack, and Microsoft Teams, which provide end-to-end encryption for meetings and chats. Additionally, utilize secure storage solutions such as Google Drive or Dropbox to store documents with the appropriate permissions.
By securing communication channels, you can mitigate the risk of interception or unauthorized access to confidential data, ensuring employee data privacy throughout the remote onboarding process.
3. Leverage Secure Access Control
Access control is a fundamental element of any cybersecurity strategy. With a remote workforce, ensuring the right level of remote access to company resources is essential. Remote workers should only have access to the information and systems necessary for their specific job roles.
To practice secure access control, use the principle of least privilege (PoLP). This implies allowing workers to get only the information and technologies that are required to perform their assignments. For instance, a customer service agent needs access to customers’ personal data on social media or a website, but must not interact with the company’s financial database.
Implement role-based access control (RBAC) to enforce these limitations effectively. RBAC assigns access permissions based on job roles, ensuring employees have the appropriate level of access for their responsibilities while minimizing risks in the event of a breach.
Integrating identity and access management (IAM) tools can be integrated to help monitor who has been given access to certain pieces of data and alert an organization should a man attempt to gain access that he is not supposed to. More so, they should incorporate the right password to apply for such accounts, and they should adhere to password policies to avoid unauthorized access.
4. Secure Endpoint Management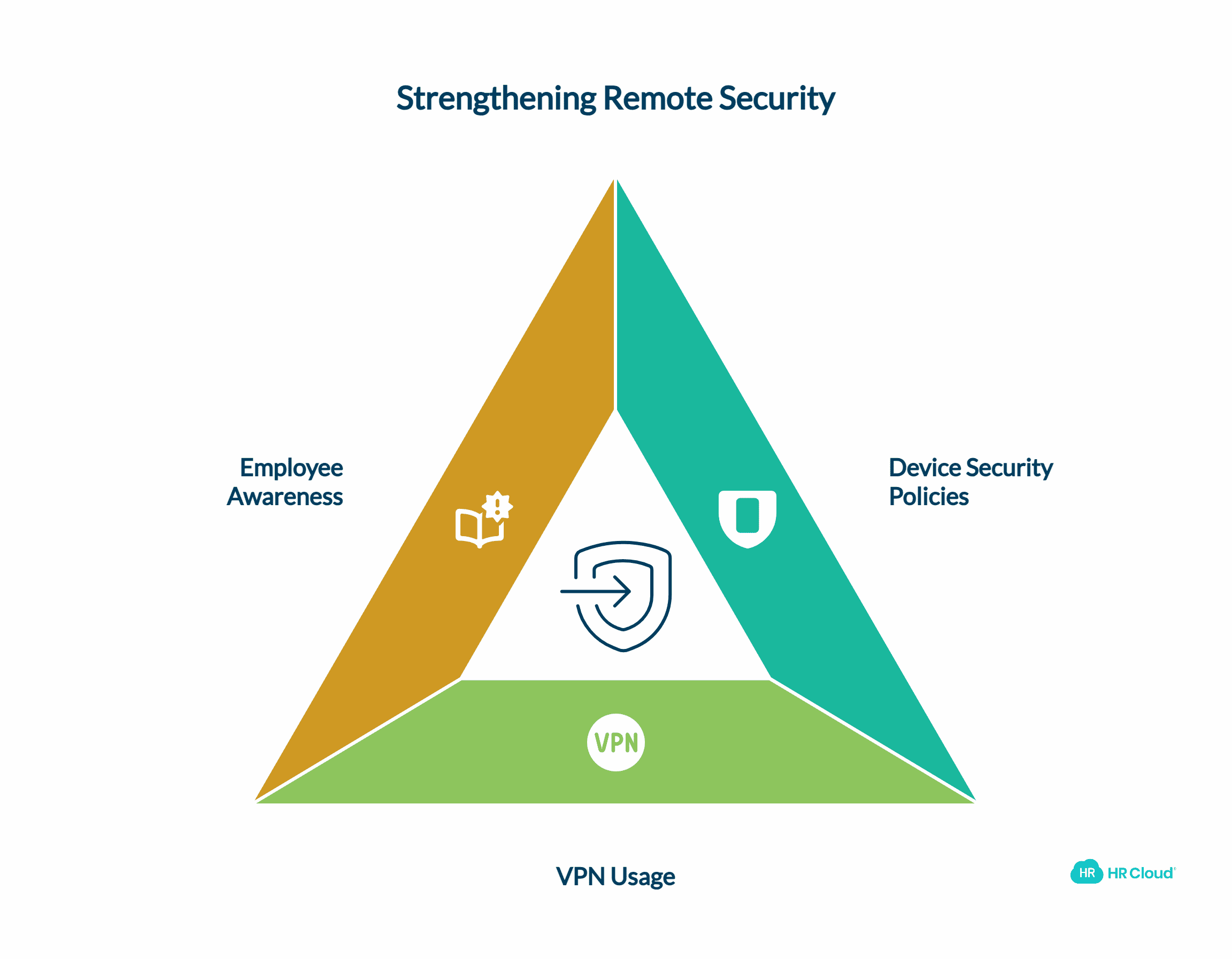
Remote employees often work on private devices, including laptops, mobile phones, or tablets. This can introduce vulnerabilities if these devices are not properly secured. To address this risk, businesses should implement endpoint management strategies as part of their digital transformation initiatives.
Endpoint security solutions enhance business control of remote employees' devices while working. These solutions can implement policies such as requiring updated virus scanners, firewalls, and encryption on all devices used for work purposes.
It’s also important to require employees to use a virtual private network (VPN) when accessing company resources remotely. A VPN, such as those highlighted in an ExpressVPN review, disguises connections by creating a secure tunnel for data transfer and protects devices from threats like man-in-the-middle attacks.
Ensure your employees are aware of security risks arising from compromised devices and adhere to best practices, including avoiding insecure Wi-Fi terminals and keeping their devices updated.
5. Provide Cybersecurity Training for Remote Hires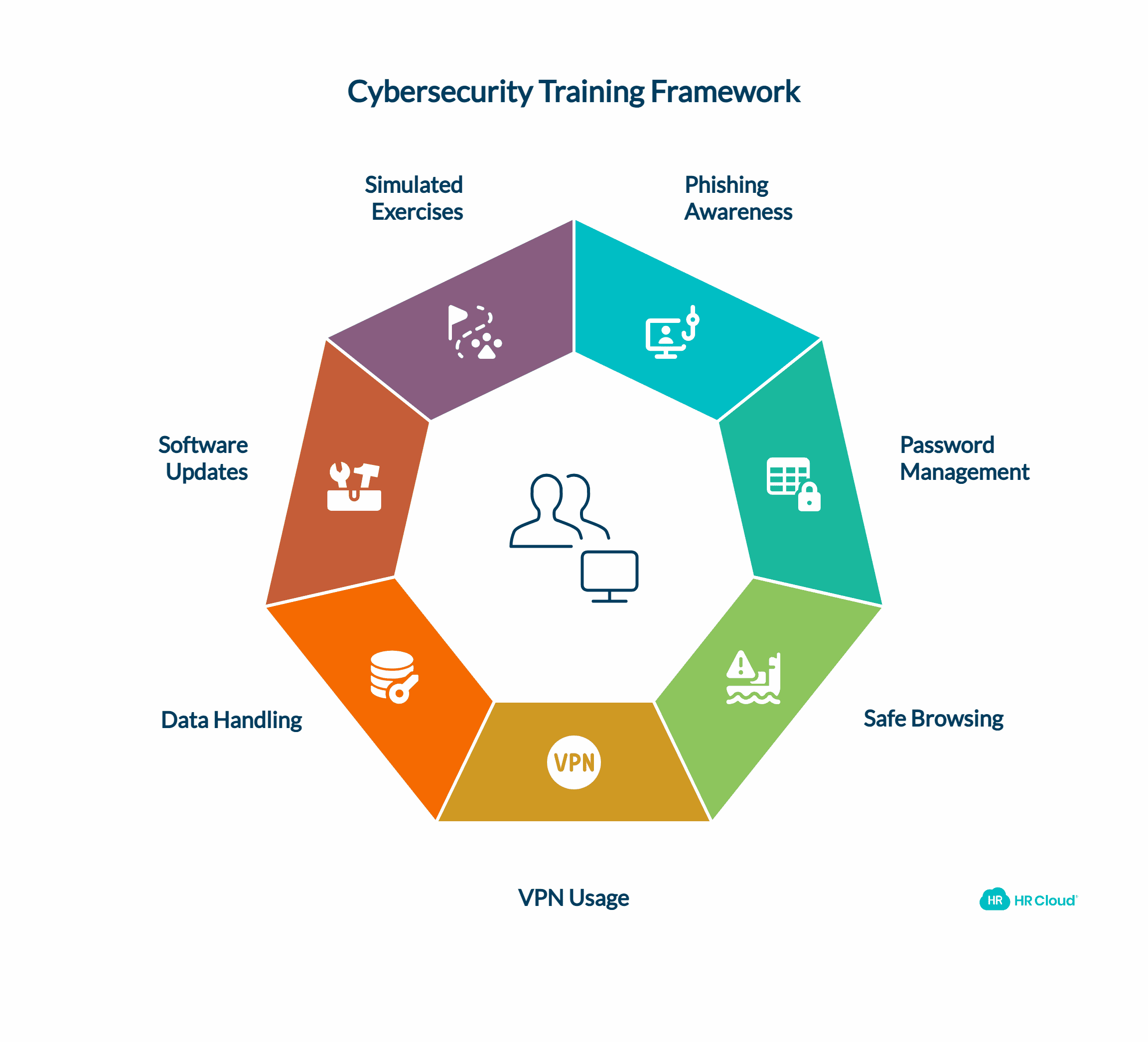
Another imperative for a secure onboarding process is the need to provide security training for people working remotely. Verizon's 2023 Data Breach Investigations Report (DBIR) mentions that many data breaches occur due to human error, such as falling victim to phishing attacks, clicking on malicious website links, or poor password compliance among employees.
With comprehensive cybersecurity training, you can minimize these occurrences and equip remote workers to better notice and even shun threats, enhancing overall security awareness.
Your training program should cover essential topics, such as:
-
Understanding and identifying phishing emails and fake websites
-
Creating strong, unique passwords and using password managers
-
Implementing good practices for browsing and downloading from the internet
-
Using VPNs on public networks
-
Handling sensitive information and proper data storage methods
-
The importance of software updates and patching vulnerabilities
Additionally, consider running simulated phishing exercises to test employees' ability to identify and avoid phishing attempts. This hands-on approach reinforces the training and helps employees become more vigilant in identifying cybersecurity threats.
6. Implement Remote Work Policies
Clear and well-structured remote work policies are essential for ensuring that remote employees follow best practices for data security. These policies should outline expectations for remote workers, such as how to handle company devices, the use of personal devices for work, and protocols for accessing sensitive data.
The policy should also include guidelines for the onboarding process, such as mandatory cybersecurity training, acceptable use of company resources, and reporting suspicious activities. Make sure employees are aware of the consequences of failing to adhere to security protocols and provide regular reminders of best practices.
Including clear policies in your employee handbooks and onboarding materials ensures that security is an integral part of your organizational culture and supports the overall digital transformation of your business.
7. Monitor and Audit Remote Employees' Activity
Continuous monitoring and auditing are essential for ensuring that remote employees adhere to your security protocols. Implementing monitoring tools allows businesses to track access to sensitive data, detect unusual behavior, and identify potential security risks before they escalate.
Security Information and Event Management (SIEM) solutions can help monitor data for security threats in real-time. These tools gather logs from endpoints, networks, and servers and raise an alarm when such logs exhibit patterns of a breach.
Regular audits of remote employees' activities help your business maintain compliance with internal and external data protection laws. Conduct compliance checks by monitoring access to restricted data and verifying that employees are following security measures. This ongoing process helps identify any weaknesses in the remote onboarding process and ensures the continued protection of sensitive information.
8. Use Digital Signatures and Contracts
Securing the remote onboarding process goes beyond preventing data loss; it also involves addressing legal and compliance factors. Digital signatures have become an essential tool for remotely signing contracts and documents securely.
Utilizing e-signatures ensures that all agreements and contracts are signed in a legally advisable and secure manner. This practice helps minimize the chances of fraud and allows organizations to meet the requirements of regulations such as GDPR and HIPAA, where needed.
Implement document verification processes to ensure the authenticity and integrity of digitally signed documents. This additional layer of security supports fraud prevention efforts and maintains the overall security of your digital onboarding process.
Conclusion
Securing the onboarding process for remote employees is a critical part of protecting sensitive data and ensuring compliance with industry regulations. By implementing robust digital identity verification, secure communication channels, and access control, businesses can create a secure environment for remote hires to thrive.
Training employees on cybersecurity, practicing ongoing monitoring activities, and leveraging digital tools are key strategies for avoiding data breaches and supporting a secure remote workforce. By implementing these onboarding best practices, companies can safely include remote candidates in their workforce without worrying about cyber threats and leaks.
Remember that secure remote onboarding is an ongoing process that requires regular updates and adaptations to address emerging threats and technological advancements. Stay informed about the latest security standards and continuously refine your onboarding practices to maintain a strong security posture in the ever-evolving landscape of remote work.
FAQ's
1. What is secure remote onboarding, and why is it important?
Secure remote onboarding is the process of integrating new employees into a company while ensuring the safety of sensitive data and compliance with regulations. It’s important because remote hires often access systems from personal devices and external networks, which increases cybersecurity risks like identity theft, data breaches, and compliance failures.
2. How can companies verify the identity of remote employees during onboarding?
Companies can use digital identity verification tools, multi-factor authentication (MFA), and biometric verification methods. MFA, for example, requires employees to confirm their identity using two or more factors—such as a password and fingerprint—making impersonation far more difficult.
3. What are the best practices for securing communication during remote onboarding?
Avoid sending sensitive data via email or open messaging apps. Instead, use encrypted channels like Microsoft Teams, Slack, or Zoom, along with secure document storage platforms (Google Drive, Dropbox) with proper permissions. This reduces risks of data leaks or interception.
4. How can organizations protect company data on remote employees’ devices?
Businesses should implement endpoint management strategies that enforce updated antivirus software, firewalls, and encryption. Employees should also be required to use VPNs to create secure data tunnels and avoid connecting through unsafe Wi-Fi networks.
5. Why is cybersecurity training essential for new remote hires?
Human error is a leading cause of data breaches. Training helps employees recognize phishing attempts, use strong passwords, follow safe browsing practices, and understand how to handle sensitive data securely. Running simulated phishing exercises can further strengthen vigilance and reduce risks.
 Discover how our HR solutions streamline onboarding, boost employee engagement, and simplify HR management
Discover how our HR solutions streamline onboarding, boost employee engagement, and simplify HR management

Keep Reading
Onboarding Adjunct Faculty and Part-Time Instructors at Scale
Adjunct faculty teach the majority of credit hours at many institutions. They're also the
A Practical Guide to Standardizing Staff Onboarding Across Multiple University Campuses
The Medical School does it one way. The Engineering Department does it another. And the
Implement Standard Blueprint for Teacher Onboarding: Ensure Equity Across Your District
Picture this: It's the first day of the new session. Two new teachers are starting in
Like What You Hear?
We'd love to chat with you more about how HR Cloud® can support your business's HR needs. Book Your Free Demo

Build a Culture of Recognition. Boost Engagement. Guaranteed.
Workmates empowers employees to stay informed, connected, and appreciated—whether they’re on the front line, in the office, or remote. Recognition drives 12x higher engagement.Trusted by industry leaders in every sector




Cut Onboarding Costs by 60%.
Take the confusion and follow-ups out of onboarding with automated workflows, digital forms, and structured portals—so new hires ramp faster 3X quicker.Trusted by industry leaders in every sector