Compliance Audit Trail
- Key Elements of a Reliable Compliance Audit Trail
- Compliance Audit Trail vs. System Log: A Comparative View
- Best Practices for Managing Your Compliance Audit Trail
- Common Pitfalls to Avoid in Audit Trail Management
- Industry Applications of the Compliance Audit Trail
- Step-by-Step Implementation Plan for a Compliance Audit Trail
- Future Outlook and Trends in Compliance Audit Trails
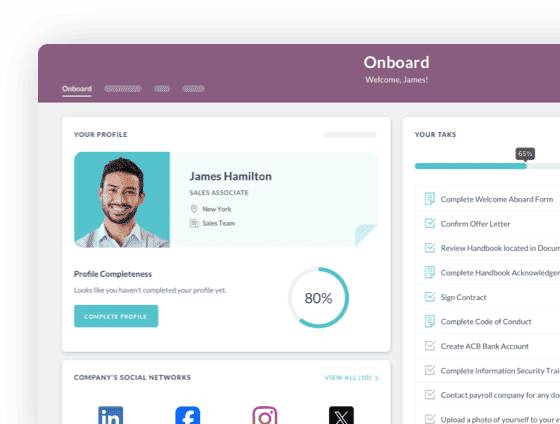
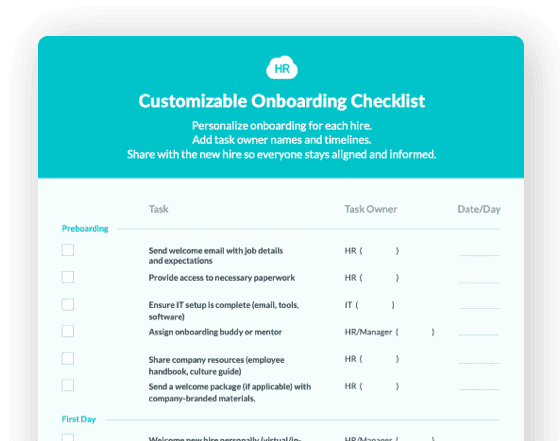
 Cut onboarding time
by 60%—here's the
Ultimate Checklist
that helped do it.
Cut onboarding time
by 60%—here's the
Ultimate Checklist
that helped do it.
A Compliance Audit Trail is a detailed, dated record. It logs every action inside a business system. These actions could affect your data or your internal rules. Think of it as a digital diary for your processes. It logs who did what, when, and how. This log is the most critical evidence a company has. Regulators, auditors, or review teams need it to see if your controls work. It proves the business operates lawfully. It is more than just a simple log. It is a structured, defensible record. It is designed specifically to ensure legal and regulatory adherence.
The main goal of a regulatory audit log is to make your work clear and checkable. In today's complex world, just intending to follow the rules is not enough. You must prove it. Without a reliable audit trail, a company cannot show that it followed legal rules. it cannot prove sensitive data is secure. It cannot show transactions were correct. This failure can bring severe fines, legal action, and a huge loss of customer trust. For leaders, a strong audit trail is not just an IT task. It is a core part of managing employee data compliance and managing risk. When a company faces a regulatory query, the audit trail's quality matters most. A good audit trail can prevent a minor review from turning into a huge penalty. For example, studies show that non-compliance costs companies much more than the money needed to manage it proactively. This means the audit trail is both a financial asset and a compliance tool.
Key Elements of a Reliable Compliance Audit Trail
A truly reliable compliance audit trail is more than just a dump of system activity. It is a strategically built data governance record. It is designed to meet specific regulatory and internal scrutiny needs.
Immutability:
The records must be tamper-proof. Once the system logs an event, no one can change or delete it. Changing it must create a new, traceable log entry. This keeps the evidence whole and trustworthy.
Time Stamping:
Every entry must have a precise, verifiable date and time. This is key to setting the sequence of events. It proves you followed time-sensitive rules.
User Attribution:
The record must clearly name the user, system, or process that started the action. This points to who is accountable. It helps you trace unauthorized or wrong activity.
Action Detail:
The log must show exactly what happened. A good entry is more than "File Edited." It should say, "User John Smith edited employee salary record for Jane Doe from $50,000 to $55,000." This gives critical internal control evidence.
Accessibility and Retrieval:
The system must let authorized staff quickly search, filter, and find specific records. They must be able to do this when auditors or legal teams ask. This efficiency is key during urgent regulatory reporting proof requests.
Retention Policy:
You must store the trail securely for the time required by relevant laws and industry standards. This time often changes for specific items like security audit files or HR compliance records.
Compliance Audit Trail vs. System Log: A Comparative View
A Compliance Audit Trail and a standard System Log both record activity. However, their purpose, structure, and legal weight are very different. You must understand this difference for proper resource planning and regulatory readiness.
|
Feature |
Compliance Audit Trail |
Standard System Log |
|
Primary Goal |
Provide regulatory reporting proof and legal evidence of adherence. |
Troubleshoot technical issues and monitor system performance. |
|
Data Scope |
Focuses on high-value, auditable events (e.g., policy changes, access to sensitive data, financial compliance logs). |
Comprehensive, often overwhelming volume of technical events (e.g., server uptime, memory usage, software errors). |
|
Retention |
Long-term, non-negotiable retention based on specific legal mandates (e.g., 7 years). |
Short-term, often cycled out quickly to save storage space. |
|
Immutability |
Mandatory. Records are protected against unauthorized modification or deletion. |
Not guaranteed. System administrators can often edit or clear logs. |
|
Audience |
Auditors, Regulators, Legal Counsel, Compliance Officers. |
IT Operations and Engineering Teams. |
Best Practices for Managing Your Compliance Audit Trail
Implementing and keeping an effective compliance audit trail requires discipline across the organization. Following these best practices makes the audit trail a strategic asset, not a burden.
Define Scope and Requirements First:
Before choosing a tool, clearly define what you must track. Base this on your industry rules (e.g., GDPR, HIPAA, Sarbanes-Oxley). You do not need to log everything, but you must log every critical, auditable event.
Automate Log Capture and Analysis:
Manual logging often leads to mistakes and missing data. Use modern HR software to streamline HR compliance and reporting. It will capture and securely date all required actions by itself. Automation also helps you watch for suspicious activity before it becomes a problem.
Implement a Least-Privilege Access Model:
Only a few trusted people should be able to view, manage, or configure the audit trail system itself. No one, not even system administrators, should be able to change or delete existing regulatory audit log entries.
Conduct Regular Internal Audits:
Do not wait for an external audit. Test your data record regularly with internal audits. This makes sure the trail is complete, correct, and easy to find. This is essential for effectively integrating your HR software. Treat your internal check like a real regulatory inspection to find any gaps.
Establish a Clear Retention and Disposal Policy:
Know the exact legal retention period for each type of compliance history tracking data. Archive older data securely. Ensure a controlled, documented disposal process when the retention rule ends.
Train Employees on Audit Trail Importance:
People are the weakest link. According to a SHRM analysis, a strong culture of compliance, backed by training, greatly lowers audit problems. Employees must know that the system tracks their actions. They must understand why this data record is key to the company’s success and security.
Common Pitfalls to Avoid in Audit Trail Management
Even well-meaning companies make mistakes. These mistakes can make their internal control evidence useless during a real audit. Knowing these traps is the first step toward reducing risk.
Over-Logging or Under-Logging:
Too much data creates "log fatigue." Critical financial compliance logs get buried in technical noise. Too little data means you miss the essential evidence needed for regulatory reporting proof. Focus on high-value, auditable events.
Lack of Independent Review:
The team that manages the system should not also manage the security audit file review. This creates a risk of bias or missed issues. An independent compliance or internal audit function should review the compliance history tracking.
Insufficient Security Measures:
The audit trail itself is very sensitive. If you do not secure it well, bad actors will target it to hide their steps. If you fail to secure this data, you fail to protect sensitive employee information.
Ignoring Time Synchronization:
Time stamps on different systems (e.g., HR, Finance, IT) must match perfectly. If they do not, the time sequence of events becomes unreliable. This makes the data governance record legally worthless.
Neglecting Employee Training:
Gallup research confirms that employee training works only if it is steady, useful, and clearly linked to business goals. If you lack continuous, role-specific compliance training, employees are more likely to make mistakes. The audit trail will just record these problems, not stop them.
 Ready to pass your next audit—without the stress? See how you can simplify compliance and eliminate gaps before they become problems.
Ready to pass your next audit—without the stress? See how you can simplify compliance and eliminate gaps before they become problems.
Industry Applications of the Compliance Audit Trail
Every regulated industry needs a reliable compliance audit trail. It is the backbone for showing accountability.
Financial Services (Sarbanes-Oxley, Dodd-Frank):
In finance, audit trails are key for transaction integrity. They must provide detailed financial compliance logs. These logs show the creation, change, and approval of every financial record. A bank's system, for instance, must show the exact order of approvals for a wire transfer. This proves that separation of duties rules were followed. This detailed tracking is critical for preventing fraud and providing internal control evidence during government checks.
Healthcare (HIPAA, HITECH):
Healthcare groups use the security audit file to track every time someone accesses Electronic Health Records (EHRs). When someone views patient data, the log must show the user ID, the time, and why they accessed it. For example, an audit trail can quickly flag an employee who views patient files without permission. This is a direct rule violation, as mandated by the Health Insurance Portability and Accountability Act (HIPAA). This tracking is key to keeping patient data private and secure.
Human Resources (GDPR, CCPA, Local Labor Laws):
For HR teams, the regulatory audit log tracks changes to sensitive employee data. This includes salary, reviews, and protected info. When securing sensitive employee information, the trail proves who approved a pay raise. It shows who accessed a discipline file. It also shows who approved a termination. A strong HR system uses the audit trail to securely track every change in employee records. This ensures that every step—hiring, firing, payroll—follows local, state, and international labor laws. This adherence is key to good records and obeying data privacy laws like GDPR. You can see how this benefits human resources operations.
Step-by-Step Implementation Plan for a Compliance Audit Trail
Switching to a strong system for compliance history tracking is a planned project. It needs cooperation from every department. Follow these steps for success with your reliable data governance record.
1. Assessment and Requirements Definition
Identify Regulatory Landscape: Map all applicable laws, standards, and internal rules (e.g., ISO, SOC 2, industry rules).
Define Critical Events: List all actions, data fields, and transactions that need a verifiable record if they change. This is the scope of your compliance audit trail.
Set Retention Policy: Document the legal retention period for each type of log data.
2. Technology Selection and Design
Choose the Right Tools: Select software that offers built-in, tamper-proof audit logging. Look for systems that help with integrating your HR software and financial systems for a single view.
System Configuration: Set up log formats to capture all five key elements: user, action, object, time stamp, and result. Make sure all logging systems use the exact same time.
3. Deployment and Testing
Pilot Program: Start the new logging system in a small, low-risk department first.
Integrity Testing: Try to tamper with the audit log files. The system must immediately find and record the unauthorized attempt.
Retrieval Testing: Act out a regulatory request. Practice quickly pulling specific, complex records. This proves the audit trail is accessible and reliable for regulatory reporting proof.
4. Training and Go-Live
Staff Education: Train all relevant employees—not just IT—on the new compliance rules. Teach them the importance of the internal control evidence and their role in keeping data honest.
Formal Policy Launch: Officially launch the new, mandatory policy. It must cover audit trail management, access control, and review procedures.
5. Ongoing Monitoring and Review
Routine Audits: Schedule frequent internal audits. Review a sample of the financial compliance logs and security audit files.
Periodic Review: Once a year, review the initial requirements. This ensures the audit trail still covers any new rules and changing business processes.
Future Outlook and Trends in Compliance Audit Trails
The world of compliance is always changing. It is driven by new technology and more complex rules. Business leaders must get their data governance record ready for what comes next.
The Rise of Blockchain and Distributed Ledger Technology (DLT):
Blockchain technology offers the best solution for immutability. Its distributed, cryptographic ledger makes tampering almost impossible. Future compliance history tracking systems may use DLT. This will give regulators verifiable, irrefutable proof of data integrity. It will further strengthen the defensibility of the regulatory audit log.
AI and Machine Learning for Proactive Monitoring:
Today, a security audit file is mostly a record of the past. Soon, Artificial Intelligence will turn it into a tool that predicts issues. AI can study huge amounts of data in real time. It will find patterns that show non-compliance or fraud before a full breach happens. The World Economic Forum highlights the growing role of AI in governance and compliance. This shifts audit trails from being just proof of the past to a tool for proactive defense. This is key to optimizing your human resources operations.
Increased Focus on Data Privacy Logs:
Global data privacy laws like GDPR and CCPA are getting stricter. The audit trail will need to log access and consent changes for individual data records more closely. Simply tracking a change is not enough. The trail must prove the change was legal and agreed upon. This detailed focus will increase the volume and complexity of the internal control evidence businesses must manage. This will require smarter systems for both capturing and finding data. Preparing for this future requires investing now in systems that prioritize detailed, secure, and easily auditable records. such as those that support automated onboarding.
Keep Reading
5 Things HR Admins Can Do Today to Improve Caregiver Retention
Caregiver turnover costs home care agencies thousands per lost employee and is sitting at
Caregiver Turnover in Home-Based Care: 5 Fixes That Actually Work
Home healthcare agencies face alarming turnover rates of 75%, with most caregivers
10 Workforce Management Issues Hospitals and Home Care Teams Face (and What Fixes Them Fast)
"We're hemorrhaging nurses faster than we can replace them, and our current
Ready to streamline your onboarding process?
Book a demo today and see how HR Cloud can help you create an exceptional experience for your new employees.

